Enhancing Cybersecurity for Web Applications: Best Practices for Developers

In today’s digital landscape, web applications are a critical part of most businesses, but they are also prime targets for cyberattacks. From data breaches to service disruptions, the consequences of poor web application security can be devastating. As cyber threats like SQL injections and Distributed Denial of Service (DDoS) attacks increase in frequency and complexity, developers must implement strong security practices to protect their applications. This article explores best practices for web application security, with a deep dive into encryption, secure coding, and proactive strategies to combat common vulnerabilities.

The data presented in the chart illustrates a significant increase in the number of cyber-attacks across various sectors, including terrorist, business, individual, and government categories, from 2000 to 2023. While attacks targeting businesses and individuals have experienced the most substantial growth, the total number of attacks has steadily risen, reflecting the increased vulnerability of different sectors to cyber threats. The sharp rise in government-related attacks, particularly from 2010 onwards, highlights the growing importance of safeguarding public infrastructure. These findings underscore the expanding threat landscape, as discussed by Harry and Gallagher (2018), Smith (2021), and IAIANI et al. (2021), who have explored the classification and impact of cyber events in various industries. More recent analyses, such as those by CSIS (2023) and Terranova Security (2024), provide updated cybersecurity statistics and trends, which support the observed growth in cyber incidents. These sources, referenced in the discussion, can be found in the reference section.
Understanding Web Application Vulnerabilities
Web applications are prone to several common vulnerabilities, including SQL injection, Cross-Site Scripting (XSS), and DDoS attacks.
- SQL injection involves inserting malicious SQL queries into an input field, allowing attackers to manipulate or gain access to the database.
- Cross-Site Scripting (XSS) occurs when hackers inject malicious scripts into web pages, which unsuspecting users then execute in their browsers, potentially exposing sensitive information.
- DDoS attacks flood a web application with excessive traffic, rendering it inaccessible.
The 2023 Verizon Data Breach Investigations Report found that 80% of cybersecurity incidents and 60% of data breaches involve web applications. These statistics highlight the urgent need for developers to adopt robust security measures to protect their applications from a constantly evolving threat landscape.
Best Practices for Enhancing Web Application Security

Developers must employ a range of security measures to defend against web-based threats, starting with secure coding practices. Secure coding helps mitigate vulnerabilities by ensuring that applications are developed in a way that resists exploitation. Following the OWASP Top 10 guidelines, which list common vulnerabilities like injection attacks and XSS, is a solid foundation.
Tools like Qualys Web Application Scanning (WAS) offer continuous, automated vulnerability detection. Unlike traditional manual assessments, Qualys WAS provides real-time insights, allowing organizations to address vulnerabilities before they can be exploited. OWASP ZAP, an open-source alternative, also offers strong vulnerability scanning capabilities, making it a viable option for developers with varying budgets.
Data Encryption for Web Applications
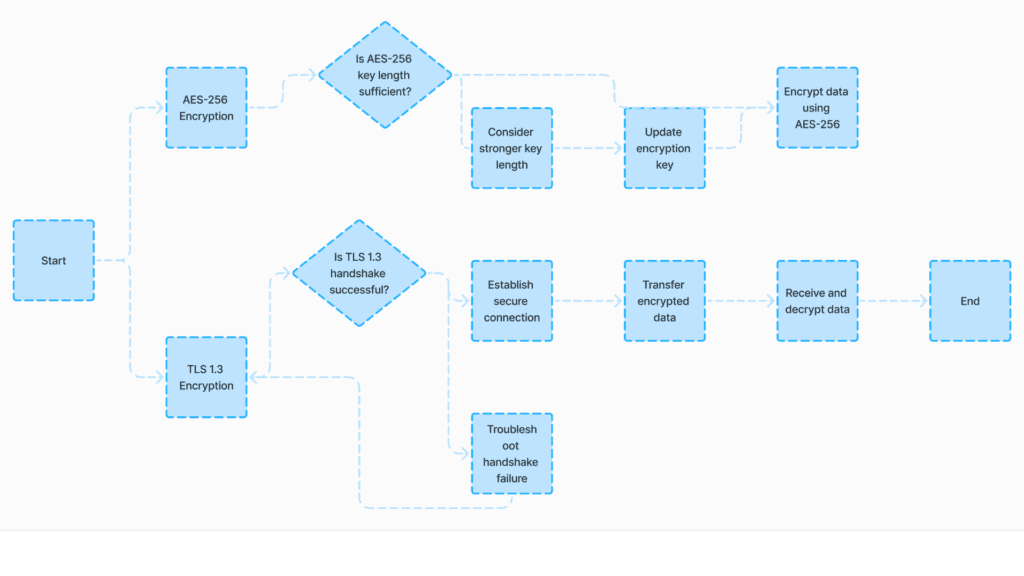
Encryption is essential for safeguarding sensitive data in web applications, both when it’s stored and transmitted. Developers should use AES-256 (Advanced Encryption Standard) to secure data at rest, providing a robust defense against unauthorized access. For data in transit, TLS 1.3 (Transport Layer Security) is recommended, as it offers enhanced security features over its predecessors, including faster handshake protocols and resistance to downgrade attacks.
A practical example comes from MetroStar, a technology firm working with U.S. federal agencies. They implemented strong encryption alongside two-factor authentication to secure web applications, replacing outdated security protocols. By adopting AES-256 and TLS 1.3, MetroStar significantly reduced vulnerabilities, ensuring compliance with Authorization to Operate (ATO) standards. Their efforts demonstrate how encryption, combined with secure authentication, can strengthen the overall security posture of an application.
Secure Authentication and Authorization

Authentication and authorization mechanisms are the first lines of defense against unauthorized access. Developers should implement Multi-Factor Authentication (MFA), which requires users to verify their identity using two or more factors (e.g., a password and a phone-based code). This significantly reduces the likelihood of an account being compromised, even if login credentials are stolen.
Role-Based Access Control (RBAC) is another critical security measure that limits access to application resources based on user roles. With RBAC, each user is assigned a specific set of permissions, ensuring that they can only access features or data relevant to their role. By enforcing strict access controls, developers can minimize the risk of privilege escalation, where attackers gain unauthorized access to sensitive parts of an application.
Input Validation and Sanitization

Input validation is vital for defending against attacks like SQL injection. Proper validation ensures that only correctly formatted data is processed by the application. Developers should also use input sanitization techniques to strip out potentially malicious code before processing it.
MetroStar again serves as a good example. They used strong input validation techniques in their development of secure web applications, ensuring that only expected data types were accepted by the system. Additionally, they implemented anti-forgery tokens to prevent Cross-Site Request Forgery (CSRF) attacks, further demonstrating the importance of input validation in preventing attacks.
Implementing Secure API Development

As web applications increasingly rely on Application Programming Interfaces (APIs), these have become a prime target for attackers. Securing APIs requires robust encryption, input validation, and rate limiting to prevent misuse or overloading by malicious actors.
Qualys WAS provides a comprehensive solution by not only securing web applications but also scanning APIs for vulnerabilities. Its continuous monitoring ensures that API endpoints are protected from threats like injection attacks and misconfigurations. For developers looking for a broader range of tools, Postman and Insomnia offer API security features such as automated testing and validation, ensuring that APIs are not only functional but also secure.
Preventing Cross-Site Scripting (XSS) Attacks

Cross-Site Scripting (XSS) attacks involve injecting malicious scripts into web applications, compromising user security. To mitigate XSS risks, developers should validate and encode user inputs to prevent the execution of unauthorized scripts.
Additionally, developers can use Content Security Policy (CSP), a security feature that defines which resources a browser is allowed to load on a page. By restricting script execution to trusted sources, CSP helps prevent attackers from injecting and executing malicious code. Implementing CSP alongside input sanitization can significantly reduce the risk of XSS attacks.
Maintaining Regulatory Compliance in Web Application Security

With regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) in place, developers need to prioritize data protection and compliance. These regulations mandate that organizations handle personal data securely and notify affected parties in the event of a breach.
Qualys WAS helps organizations maintain compliance by identifying vulnerabilities that could lead to data breaches. Its automated scanning and reporting features make it easier to track compliance with both internal security policies and external regulations.
Using Web Application Firewalls (WAF)

A Web Application Firewall (WAF) is essential for protecting web applications from various external threats, such as SQL injections, DDoS attacks, and XSS attempts. WAFs monitor and filter HTTP traffic, blocking malicious requests before they reach the application.
DataDome, a cybersecurity company specializing in bot protection, uses WAF technology to inspect real-time traffic and prevent automated attacks. Their WAF solution helps ensure the availability and security of web applications by filtering out malicious traffic. Alternatives like Cloudflare also provide powerful WAF solutions, combining DDoS protection and traffic filtering for comprehensive security.
As cyber threats evolve, securing web applications is no longer a choice—it’s a necessity. Developers can protect their applications by adopting encryption protocols like AES-256 for data at rest and TLS 1.3 for data in transit, implementing strong authentication mechanisms such as MFA, and continuously monitoring their applications for vulnerabilities. Tools like Qualys WAS, OWASP ZAP, and DataDome provide essential security infrastructure, allowing developers to identify and address threats in real time.
Start by evaluating your current security measures and integrating proactive solutions today. By implementing secure coding practices, continuously monitoring for vulnerabilities, and managing third-party dependencies carefully, developers can significantly reduce the risk of cyberattacks and protect both users and data.
